Hackers are exploiting a fake Bitdefender website to distribute three different malware programs simultaneously, demonstrating how criminals now build custom attack tools from freely available components.
The malicious site, “bitdefender-download[.]com,” copies Bitdefender’s legitimate antivirus download page to trick users into installing VenomRAT, StormKitty, and SilentTrinity malware. DomainTools Intelligence researchers discovered the campaign in late May 2025.
“This campaign underscores a constant trend: attackers are using sophisticated, modular malware built from open-source components,” said DomainTools researchers. “This ‘build-your-own-malware’ approach makes these attacks more efficient, stealthy, and adaptable.”
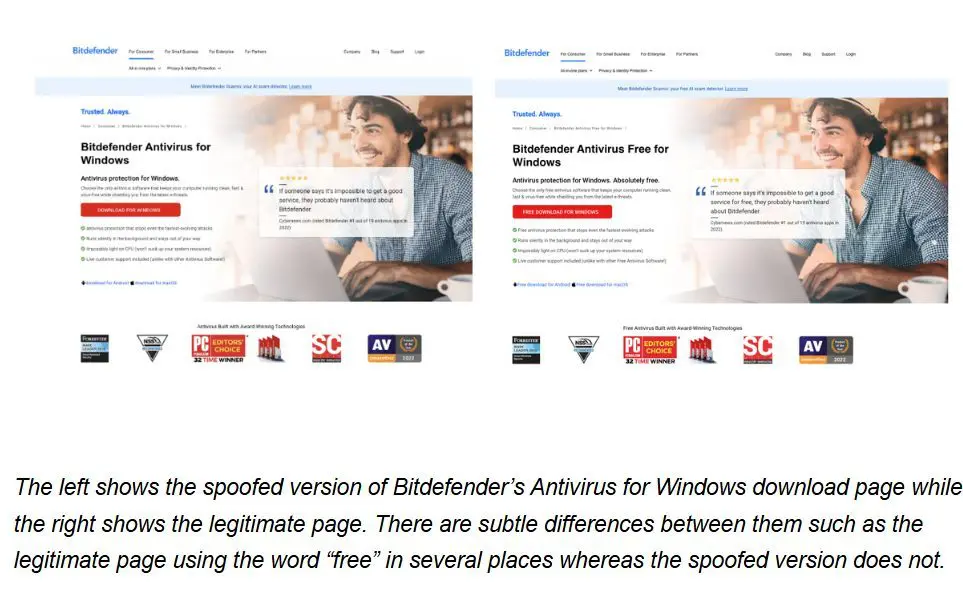
The fake website appears nearly identical to Bitdefender’s official download page. However, clicking the “Download for Windows” button triggers a malicious file download from Amazon S3 servers.
Source: DomainTools Intelligence
Users receive a ZIP file containing “StoreInstaller.exe.” This executable bundles three separate attack tools that work together. VenomRAT provides remote system access. StormKitty steals passwords and cryptocurrency wallet information. SilentTrinity maintains hidden, long-term control.
Each malware component comes from open-source projects available to anyone online. VenomRAT originated as a modified version of Quasar RAT. Both StormKitty and SilentTrinity use publicly available code frameworks.
This modular approach allows criminals to quickly assemble powerful attack tools without advanced programming skills. They can mix and match components based on their specific targets and goals.
Researchers traced multiple malware samples to the same attackers using shared command-and-control servers. The primary server operates at IP address 67.217.228.160 on port 4449.
The fake Bitdefender site connects to other fraudulent websites targeting financial institutions. Related domains impersonate Armenian IDBank, Royal Bank of Canada, and Microsoft login pages.
“These criminals are after your hard-earned money, targeting your bank accounts and cryptocurrency wallets with fake login pages and malware disguised as safe software,” DomainTools warned.
The attack demonstrates how cybercrime has become more accessible through open-source tools. While security researchers can identify these components more easily, criminals benefit from faster development and deployment.
Google Chrome now flags the malicious download link, preventing most users from accessing the fake software. Bitdefender confirmed the fraudulent site is not operated by the company and said they are working to shut it down.
Security experts recommend downloading software only from official websites and verified sources. Users should verify website addresses carefully, especially for banking and login pages.



















