Encryption is one protective tool at your disposal and scrambles your data so nobody can listen in. Hotspots, chat, voice, email, and texts can be encrypted through Android-available tools.
Public Wi-Fi Networks
Hotspots can be spoofed, leading you to connect to data-sucking criminals lurking nearby. In the United States, data is inherently insecure when wafting around coffee shops and other public networks.

There’s a simple way to protect yourself. However, that’s to camouflage your wireless data via encryption and create a private tunnel through the Internet. It’s called a Virtual Private Network. VPNs can be used to encrypt all of your public hotspot data traffic, including bank transactions and so on. And it also conveniently protects those celebrities amongst us from prying gossip vendors. Search for VPN in Play Store, and Private Tunnel will give you 100MB of data transfer to try it out. After that, a 50GB chunk is $12.
Voice Calls and Texts
Suppose you’re concerned that the interception of your phone calls by world leaders, human rights groups. Or your spouse may create a diplomatic incident. In that case, you can encrypt your calls and texts. The Guardian project’s open-source mobile privacy developer has been working on several solutions. You can experiment by downloading and configuring the calling-app Sipnetic. Silent Circle’s Silent phone app is a robust alternative.
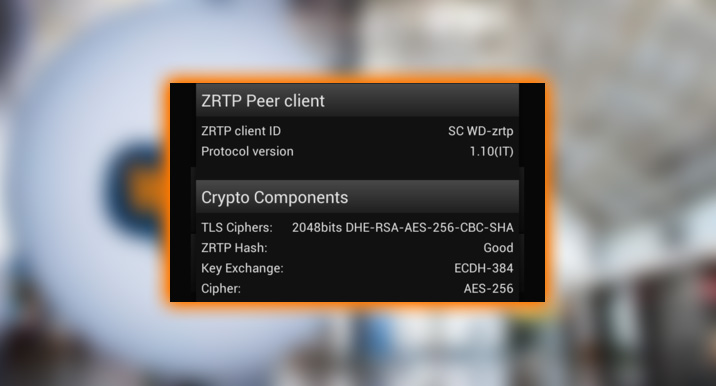
The Silent Circle Mobile package, including video and 100 MB document sending, costs $10 a month.
Orbot
Encrypting your communications doesn’t necessarily require monthly fees, though. That’s capitalistic for the average oppressed dissident. If you are one and want to explore the world of encrypted communications on the cheap, you can always use Orbot. Orbot scrambles your Internet traffic, then bounces it worldwide using Tor Project.
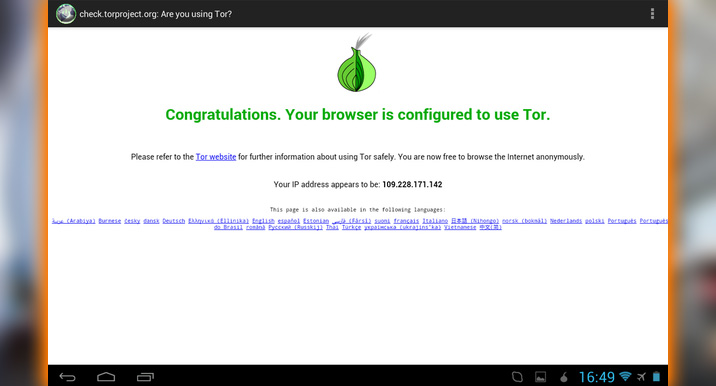
Bouncing hides your originating location. Coupling that with encryption helps create secure communications. The Orbot app combines web browsing, chat, and email. However, ChatSecure failed to work with accounts when I tried it. So you should try other Orbot apps before taking on that project. I’d start with Ostel’s voice calling. It worked for me.
Android Privacy Guard, or Open PGP solution for encrypting your email. It is more straightforward than the Guardian Project’s Gnu Privacy Guard. And it is excellent at derailing any attempted hacker eyes dropping. On the latest corporate acquisition can happen when you’re not careful.
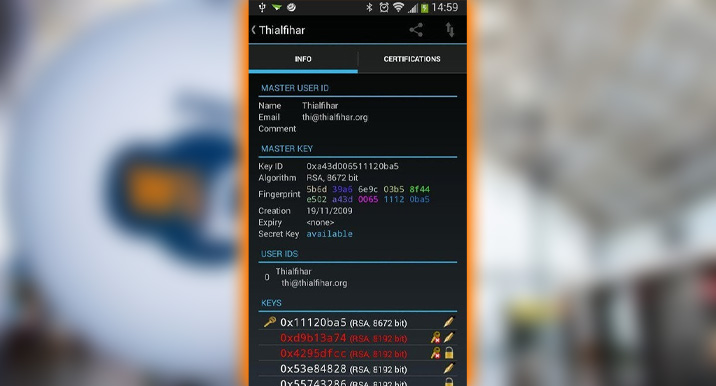
Use the OpenPGP app alongside the encryption-friendly Android email client app or K-9 Mail. Create and manage keys in the App. Then use K-9 to compose emails. Choose encryption and your stored keys as an email-sending option.
Communications Downsides
Once you’ve got your head around the idea. Both the sender and recipient have a key to encrypt, decrypt, and sign emails. It’s easy to implement encryption for your daily correspondence. The main drawback to communicating with encryption is that both parties must have encryption-enabled apps. For private communications to work securely. This is a particularly intrusive issue when it comes to voice calls. If you’re a lawyer, say, and want to have a private voice conversation with your neighborhood whistleblower. You’ll need to install a compatible app with purchase plans before discussing some dastardly multinational’s evil deeds, like groundwater contamination. That’s if you want to be sure the suits don’t listen in.
Backdoors
And finally, here’s a warning: Government-requested back-doors are not unheard of in encryption tools. So, watch out, or you might live in a Russian airport for a while.














